Like many others, it permits the connection to the Tor network. However, this is not a complete anonymous networking platform. This is a method to protect users from possible attacks.
Can Search Engines Find Everything On The Dark Web?
All those are pre-configured, keeping in mind the anonymity and security. It also implements the darknet technology and a decentralized file storage system for helping its users remain anonymous, just the way Bitcoin (BTC) works. I2P is the acronym for the Invisible Internet Project that permits you to access the internet without a hassle both on the dark web and surface web via a layered stream. It offers the most secure ways to start browsing on the dark web.
If you feel a browser just won’t cut it and want to keep your dark web browsing activity as private as possible, Whonix might be for you. Remember that activity within apps you’re logged into will be recorded, even if you’re using Tor. Orbot is free, open source, and can even replace your VPN, if you don’t mind slower browsing speeds. It is worth noting that Private window with Tor isn’t as secure as using the Tor Browser itself.
Subscribe To A Formidable VPN
Its user interface, resembling Firefox ESR, provides a familiar gateway to dark web sites utilizing the .onion domain. Traffic undergoes multiple layers of encryption, thwarting interception and monitoring attempts. Here, we provide the top ten darknet browsers of 2023, which have been carefully compared to industry standards for privacy, security, and usability. Through the use of onion routing and many layers of encryption to conceal users’ names and locations, darknets provide secret and anonymous communication.
How Tor Browser Works
Specifically, the I2P darknet is accessible, while the Tor network is accessible through the Orchid Outproxy Tor plugin. The US Naval Research Laboratory developed The Onion Routing (Tor) project in the late 90s. However, technological advancements such as encryption and privacy-focused browsers like Tor enabled the general public to access it. For example, you can find information unavailable to the public and share data privately while protecting your online identity. Tor and I2P are the two commonly used tools for accessing the dark web to provide anonymity.
JPMorgan, Citi, Morgan Stanley Assess Fallout From SitusAMC Data Breach
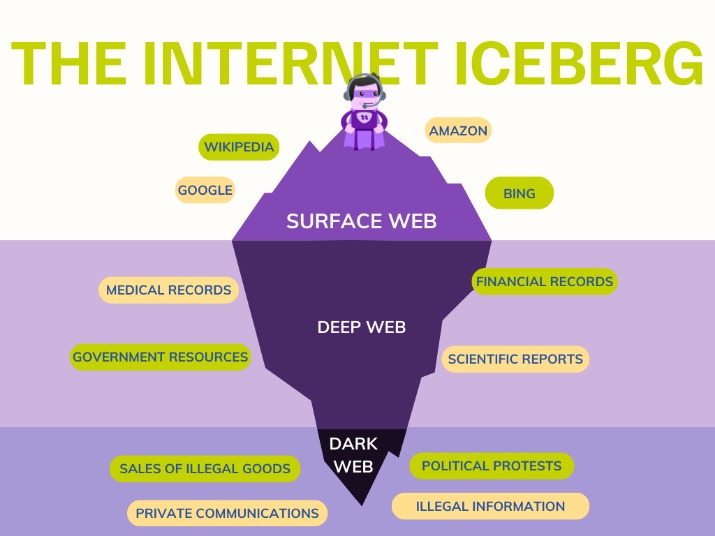
If they control enough nodes and correlate timing patterns, they can trace traffic back to specific users. 60% of dark web domains host illegal content (Panda Security). The Tor network hosts over 65,000 .onion URLs (TrueList). The deep web is 90-95% of the internet that search engines don’t index, like your email and bank account. Cybersecurity researchers have uncovered a dangerous tool causing a stir on the dark web and within GNUnet isn’t just a browser—it’s more of a platform for building decentralized networks.

What Is The Safest Dark Web Search Engine?
Tor doesn’t support external plugins and extensions, unlike standard browsers. They facilitate secure communication over the web and protect from third-party surveillance. The above configurations help improve your security when surfing the web via Tor. This feature can’t be changed because it’s integral to Tor’s privacy focus. You should avoid downloading files via Tor to maximize your anonymity. To maximize security, you should avoid logging into personal accounts, such as Facebook and Gmail, via Tor.
Types Of Dark Web Sites (and What Really Goes On There)

Also, the final relay of the Tor network is not encrypted, meaning that traffic between the exit node and destination server could be monitored. While Tor Browser enhancing your anonymity online, it does not protect users from all dangers of the web. The Tor network routes TCP traffic of all kinds but is optimized for web browsing. If you’ve never used Tor, the first thing you’ll notice is that it’s slow — or at least, slower than regular internet browsing. And yes, some Tor users leverage the browser to bypass restricted contact, consume illegal materials, or participate in illegal activities.

- Google’s purpose is to show the most relevant information to all of its users quickly and easily.
- Therefore, users must approach all onion links with a high degree of skepticism and take measures to verify their authenticity whenever possible.
- For deeper access or full Tor anonymity, you can also stack NordVPN with the Tor browser for double encryption, and during testing, everything stayed stable.
- Unlike Tor’s global network, I2P operates as a more localized, peer-to-peer network.
The exit node removes the final layer of encryption on your data. The folder will be named “tor-browser_en-US” if you are running the English Tor Browser. In the App Store, click “GET” to download the browser. The “Onion Browser” is available in the App Store.
Best Sites For Free NFL Streaming Games
For users intending to browse the dark web, it is generally recommended to increase the security level to at least “Safer,” and ideally to “Safest,” to minimize the risk of encountering malicious scripts and other threats. The “Safer” level disables certain website features that are often exploited for malicious purposes, such as JavaScript on non-HTTPS sites, and requires click-to-play for audio and video content. Clicking this button will lead to a series of configuration options designed to help users bypass censorship or accommodate specific network setups. At the heart of Tor Browser’s functionality lies the Tor network and the principle of onion routing.
Navy Research Laboratory initially developed to protect government communications before it later made it publicly available. This guide provides an in-depth, unbiased review of the top secure hidden internet browser options available in 2025. Living in a world where surveillance takes place, where you face constant threats almost daily, and where censorship reigns supreme requires tools to reclaim your privacy and security. Antidetect browsers are powerful tools that let you mask your digital fingerprints and manage multip… The Tor browser offers strong online protection, given that it routes your online traffic via severa… The safest and best dark web browsing tool for Android users is the official Tor Browser APK from the Tor Project site.
Plus, I don’t think that torrenting over Tor is secure, as some Tor servers can see your IP address, which is terrible for your privacy. However, the first Tor server you connect to can see your real IP address — if a malicious actor operates it, they could collect it and use it to track your location or online behavior. A VPN is an online app that also changes your IP address and encrypts your traffic — but it only does it once, which allows VPNs to provide much faster speeds than Tor.
This encrypted data is then randomly bounced through a series of relays, operated by volunteers across the globe. Download Avast Secure Browser today for better security, control, and performance. Tor recommends iOS alternatives, Onion Browser or Orbot, for open-source browsers that use similar technology to Tor.



